Vulnerability Scanning in your CI/CD Pipeline - Part Two
Por um escritor misterioso
Last updated 26 outubro 2024

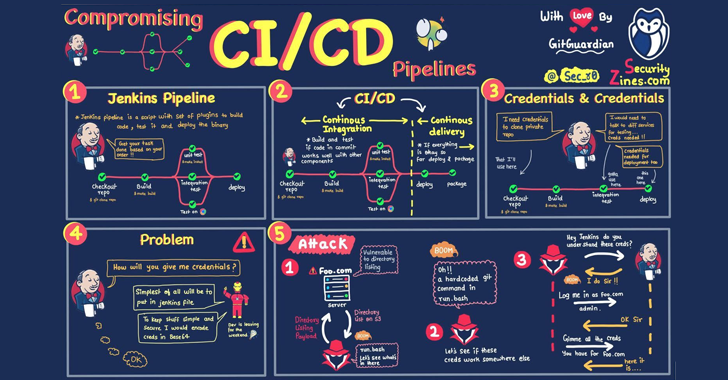
CI/CD Risks: Protecting Your Software Development Pipelines

CI / CD Pipeline Integrations

Getting Started With CI/CD Pipeline Security - DZone Refcardz

Adding Image Scanning into your CI/CD Pipeline

Vulnerability scans on Kubernetes with Pipeline

Implement DevSecOps to Secure Your CI/CD Pipeline

Vulnerability Scanning in your CI/CD Pipeline - Part Two
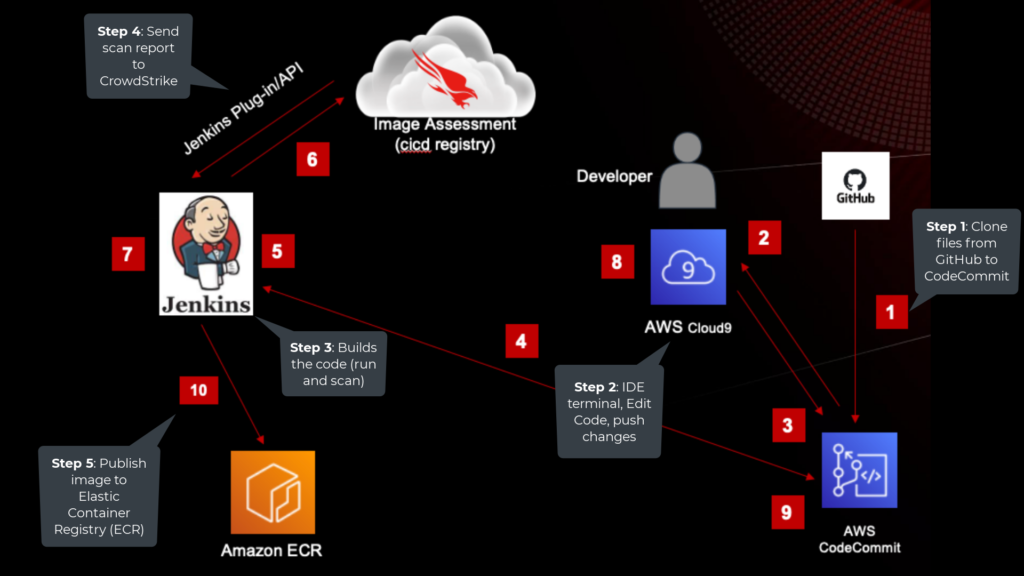
Securing your Jenkins CI/CD Container Pipeline with CrowdStrike

Raven: Open-source CI/CD pipeline security scanner - Help Net Security
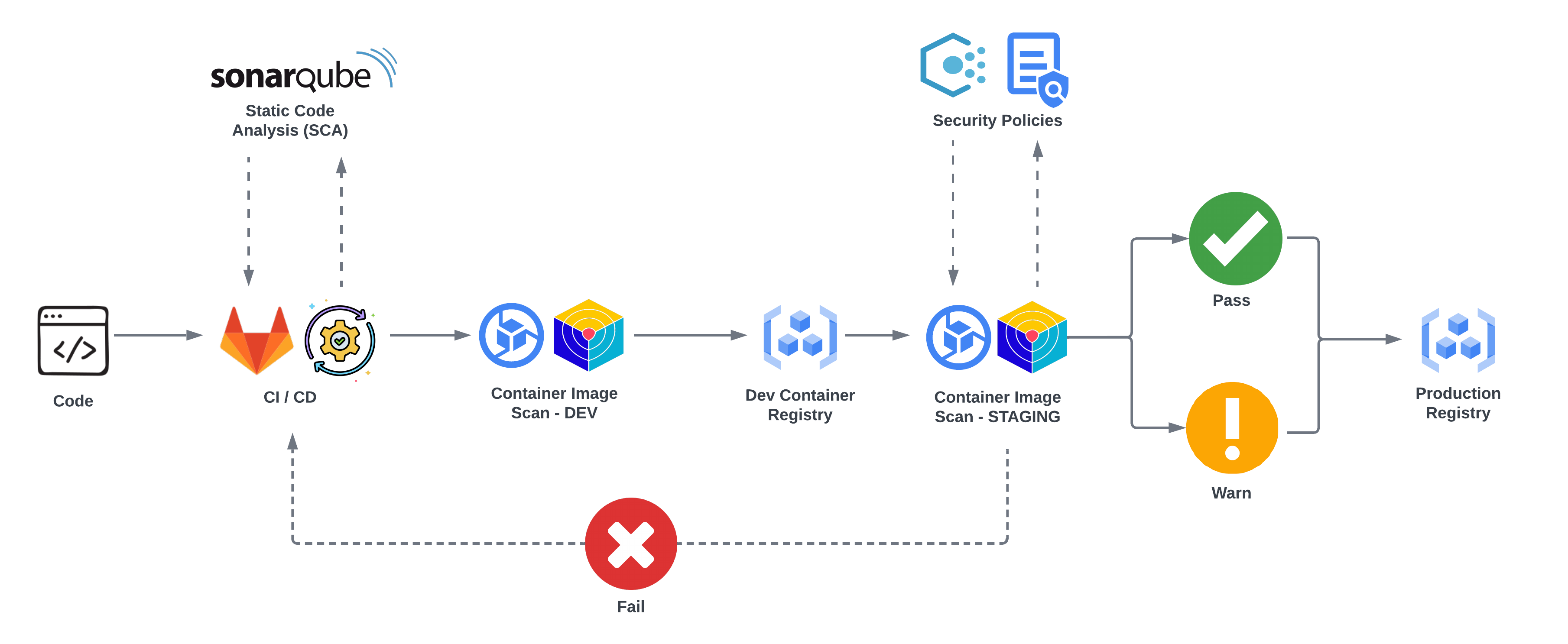
Adroit Cloud Consulting
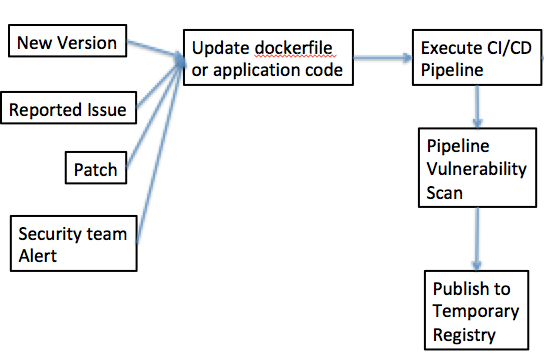
Pipeline Vulnerability Scanner - Cloud Adoption Patterns
Recomendado para você
-
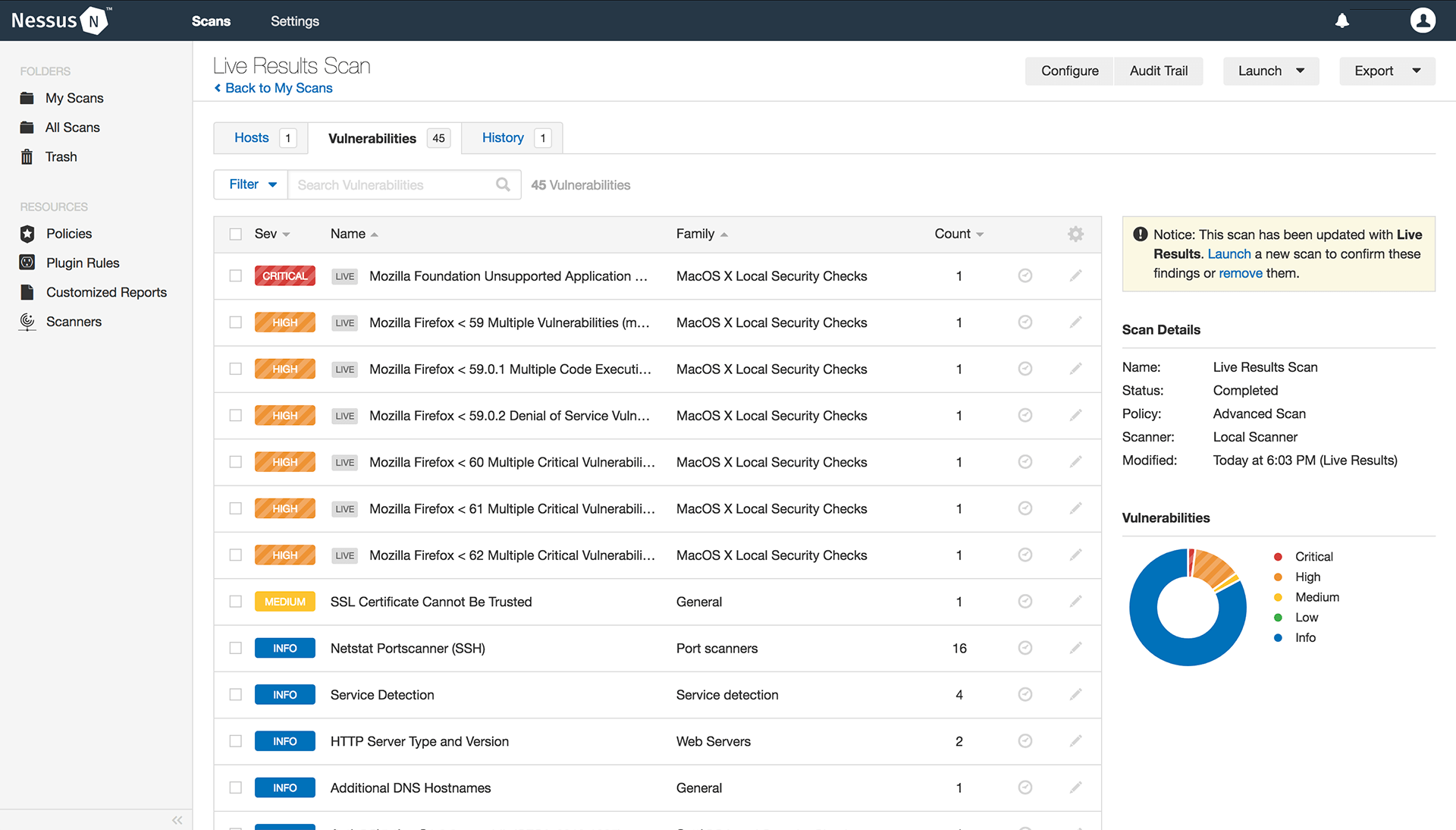 Advanced Vulnerability Assessment with Nessus Professional26 outubro 2024
Advanced Vulnerability Assessment with Nessus Professional26 outubro 2024 -
Nexus iOS26 outubro 2024
-
Nexus iOS - Nexus Scan Gauges allow for full-arch26 outubro 2024
-
 AurumTek® Implant Bridge powered by Nexus iOS - The Aurum Group26 outubro 2024
AurumTek® Implant Bridge powered by Nexus iOS - The Aurum Group26 outubro 2024 -
.png?alt=media&token=ab808906-5893-4dff-a609-a3508f1375b4) Nexus Repository Manager Gatekeeper Plugin - Snyk User Docs26 outubro 2024
Nexus Repository Manager Gatekeeper Plugin - Snyk User Docs26 outubro 2024 -
 SCAN (SDG & Climate Action Nexus) tool: Linking Climate Action and the Sustainable Development Goals26 outubro 2024
SCAN (SDG & Climate Action Nexus) tool: Linking Climate Action and the Sustainable Development Goals26 outubro 2024 -
 NeXus file structure showing the NXtomo subentry expanded to show26 outubro 2024
NeXus file structure showing the NXtomo subentry expanded to show26 outubro 2024 -
Curious as to how to go about implementing Nexus IOS system into your workflow? Here's a quick instructional video on the novel technique and technology,, By Gdental26 outubro 2024
-
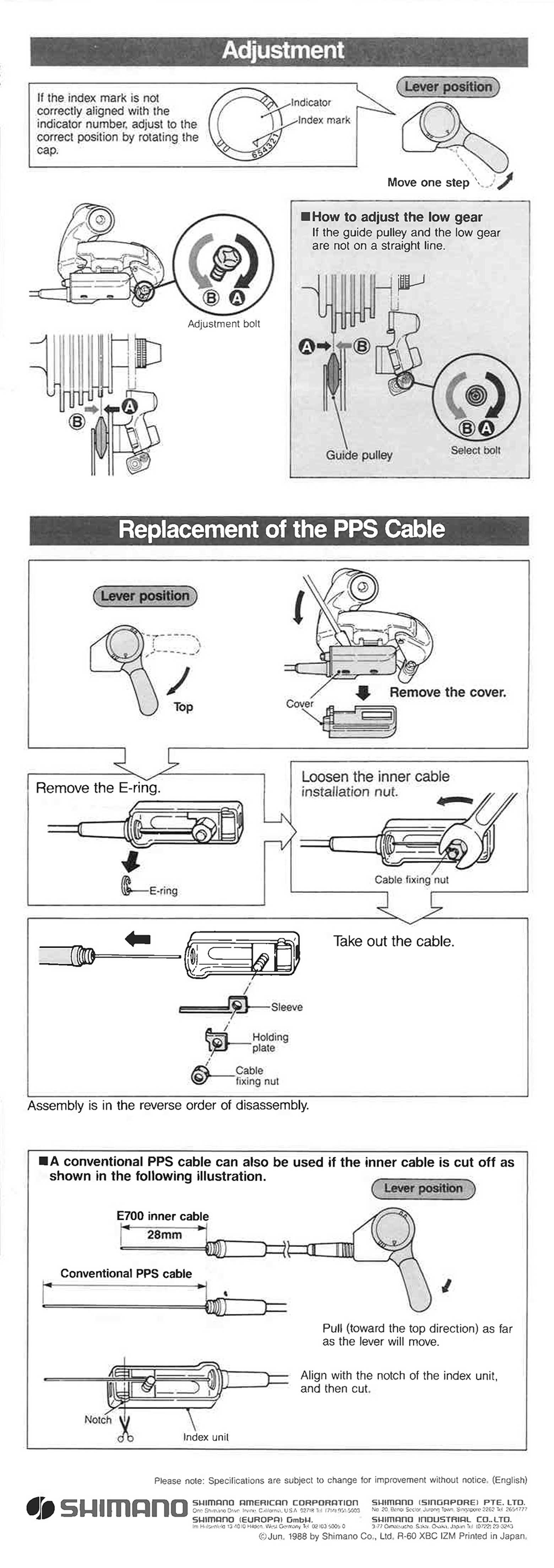 Shimano - Service Instructions Nexus RD-E700 Rear Derailleur scan 226 outubro 2024
Shimano - Service Instructions Nexus RD-E700 Rear Derailleur scan 226 outubro 2024 -
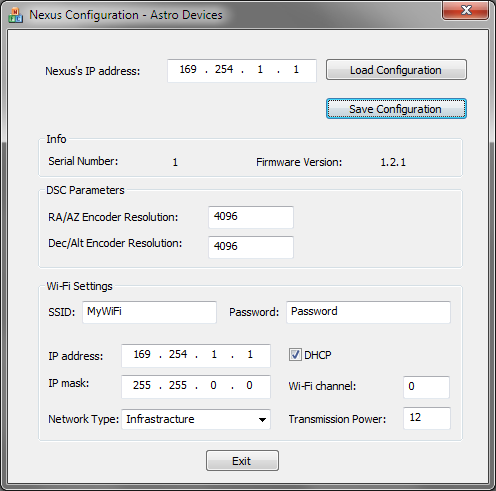 Nexus & Windows26 outubro 2024
Nexus & Windows26 outubro 2024
você pode gostar
-
 Shadow Island – Lost Ark Walkthrough Guide - MMOPIXEL26 outubro 2024
Shadow Island – Lost Ark Walkthrough Guide - MMOPIXEL26 outubro 2024 -
 Samsung Galaxy S21 Ultra 5G G9980 12/256GB DS Snapdragon 888 6.8 IP68 By FedEx26 outubro 2024
Samsung Galaxy S21 Ultra 5G G9980 12/256GB DS Snapdragon 888 6.8 IP68 By FedEx26 outubro 2024 -
 The Legend of Zelda (1986) - MobyGames26 outubro 2024
The Legend of Zelda (1986) - MobyGames26 outubro 2024 -
 B.A.A. Half Marathon 2018: Full Results26 outubro 2024
B.A.A. Half Marathon 2018: Full Results26 outubro 2024 -
 Spy Classroom and Kubo Won't Let Me Be Invisible Kick-Off HIDIVE's Upcoming Winter Simulcasts Included in Exciting Lineup of Eight New Titles For 202326 outubro 2024
Spy Classroom and Kubo Won't Let Me Be Invisible Kick-Off HIDIVE's Upcoming Winter Simulcasts Included in Exciting Lineup of Eight New Titles For 202326 outubro 2024 -
/i.s3.glbimg.com/v1/AUTH_08fbf48bc0524877943fe86e43087e7a/internal_photos/bs/2021/I/3/FXeapkQhAPNe2iSRU90Q/2016-07-07-poke-go-1.jpg) Como evoluir os Pokémon em Pokémon Go26 outubro 2024
Como evoluir os Pokémon em Pokémon Go26 outubro 2024 -
Steam Workshop::Level Fun Backrooms26 outubro 2024
-
 Casa com Jardim Peppa Pig - DTC - Ri Happy26 outubro 2024
Casa com Jardim Peppa Pig - DTC - Ri Happy26 outubro 2024 -
 Grand Blue Capítulo 86 – Mangás Chan26 outubro 2024
Grand Blue Capítulo 86 – Mangás Chan26 outubro 2024 -
 Download & Play Angel Legion: 3D Hero Idle RPG on PC & Mac26 outubro 2024
Download & Play Angel Legion: 3D Hero Idle RPG on PC & Mac26 outubro 2024


