Cybercriminals are circumventing email security with image-based
Por um escritor misterioso
Last updated 23 outubro 2024
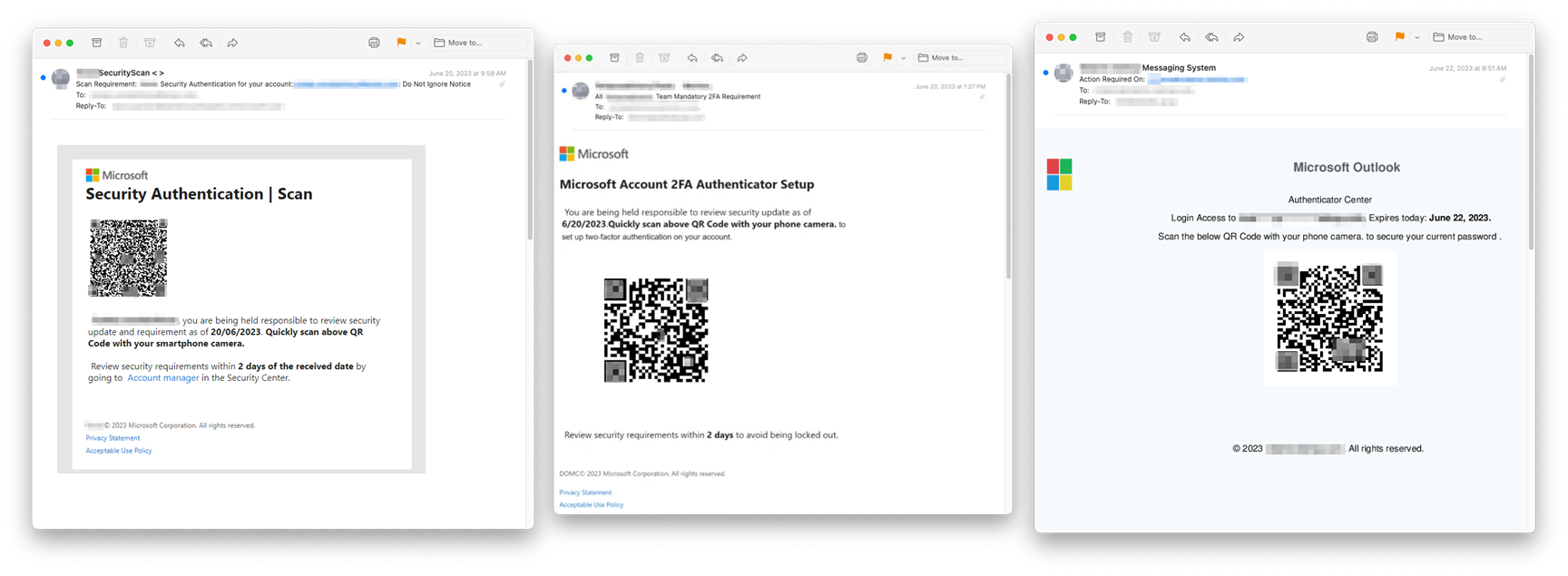
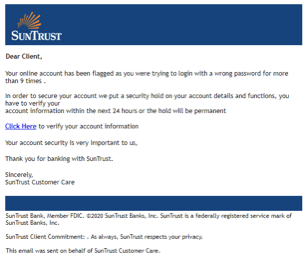
Security researchers at Inky recently discovered a rash of fraudulent emails that bypass certain conventional spam filters by using image attachments and QR codes. The scams don't
Security researchers at Inky recently discovered a rash of fraudulent emails that bypass certain conventional spam filters by using image attachments and QR codes. The scams don't
Security researchers at Inky recently discovered a rash of fraudulent emails that bypass certain conventional spam filters by using image attachments and QR codes. The scams don't
Remote Images Are Pushing Email Filters to Their Limits

Microsoft takes legal action against COVID-19-related cybercrime - Microsoft On the Issues

4 best email security tools you need in your stack

Cybercriminals use reverse tunneling and URL shorteners to launch 'virtually undetectable' phishing campaigns
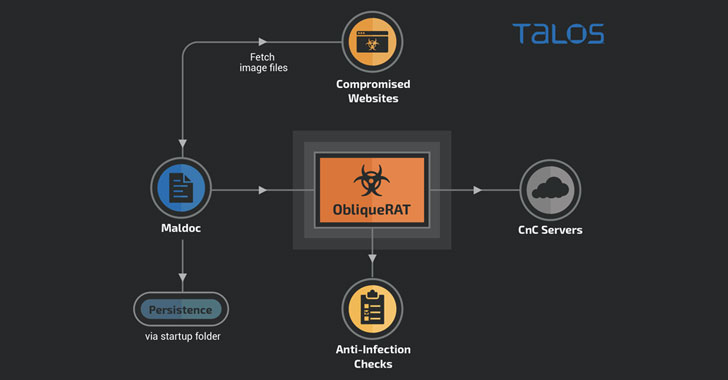
Hackers Now Hiding ObliqueRAT Payload in Images to Evade Detection

IBM Security: Cybercriminals focusing on cryptojacking

Microsoft: BEC Attackers Evade 'Impossible Travel' Flags With Residential IP Addresses
20 Eye-Opening Cybercrime Statistics

What Is Email Security? Definition, Benefits, Examples & Best Practices - Spiceworks
Recomendado para você
-
 Roblox music codes, The best song IDs to use23 outubro 2024
Roblox music codes, The best song IDs to use23 outubro 2024 -
 Roblox: Códigos de Evasão (outubro de 2023) - CenárioMT23 outubro 2024
Roblox: Códigos de Evasão (outubro de 2023) - CenárioMT23 outubro 2024 -
Codes, Roblox Evade Wiki23 outubro 2024
-
 Roblox Evolution Evade Codes (December 2023) - Pro Game Guides23 outubro 2024
Roblox Evolution Evade Codes (December 2023) - Pro Game Guides23 outubro 2024 -
 NEW* ALL WORKING CODES FOR EVADE IN MARCH 2023! ROBLOX EVADE CODES23 outubro 2024
NEW* ALL WORKING CODES FOR EVADE IN MARCH 2023! ROBLOX EVADE CODES23 outubro 2024 -
 Evade codes December 2023 - PROJAKER23 outubro 2024
Evade codes December 2023 - PROJAKER23 outubro 2024 -
 The Nerd Stash on X: Roblox Evade Codes (March 2023) #guide23 outubro 2024
The Nerd Stash on X: Roblox Evade Codes (March 2023) #guide23 outubro 2024 -
 Utilizing Morse Code to Evade Signature Based Detection Systems23 outubro 2024
Utilizing Morse Code to Evade Signature Based Detection Systems23 outubro 2024 -
 Full code Evade Roblox mới nhất 2023, cách nhập code23 outubro 2024
Full code Evade Roblox mới nhất 2023, cách nhập code23 outubro 2024 -
 College Presidents Under Fire After Dodging Questions About23 outubro 2024
College Presidents Under Fire After Dodging Questions About23 outubro 2024
você pode gostar
-
Handmade Lamps23 outubro 2024
-
 Minigincana: 10 ideias de brincadeiras para pequenos espaços23 outubro 2024
Minigincana: 10 ideias de brincadeiras para pequenos espaços23 outubro 2024 -
 Booth Theatre in Independence, KS - Cinema Treasures23 outubro 2024
Booth Theatre in Independence, KS - Cinema Treasures23 outubro 2024 -
 Update: Among Us Available Now with Xbox Game Pass for PC, Coming 2021 to Xbox Game Pass for Console - Xbox Wire23 outubro 2024
Update: Among Us Available Now with Xbox Game Pass for PC, Coming 2021 to Xbox Game Pass for Console - Xbox Wire23 outubro 2024 -
 51gV6ijprmL._CLa, 667,500, 51CBoVtI4QL.jpg23 outubro 2024
51gV6ijprmL._CLa, 667,500, 51CBoVtI4QL.jpg23 outubro 2024 -
 TODO DIA UM PERSONAGEM DE ANIME on X: 172 - Ninym Ralei (Tensai23 outubro 2024
TODO DIA UM PERSONAGEM DE ANIME on X: 172 - Ninym Ralei (Tensai23 outubro 2024 -
 Sonic the Hedgehog: The Movie / Awesome - TV Tropes23 outubro 2024
Sonic the Hedgehog: The Movie / Awesome - TV Tropes23 outubro 2024 -
The amazing Killer Sans (@the_amazing_killer_sans)23 outubro 2024
-
 Random: Zelda Devs Reveal Which Link They Think Is The Stinkiest23 outubro 2024
Random: Zelda Devs Reveal Which Link They Think Is The Stinkiest23 outubro 2024 -
PiScEs27 AKA: Gandalf's Apprentice on X: Founders of Hogwarts (Fancast) Ewan McGregor as Godric Gryffindor Mark Strong as Salazar Slytherin Katie McGarth as Rowena Ravenclaw Hayley Atwell as Helga Hufflepuff /23 outubro 2024



