Threats & Research Archives - F-Secure Blog
Por um escritor misterioso
Last updated 28 outubro 2024

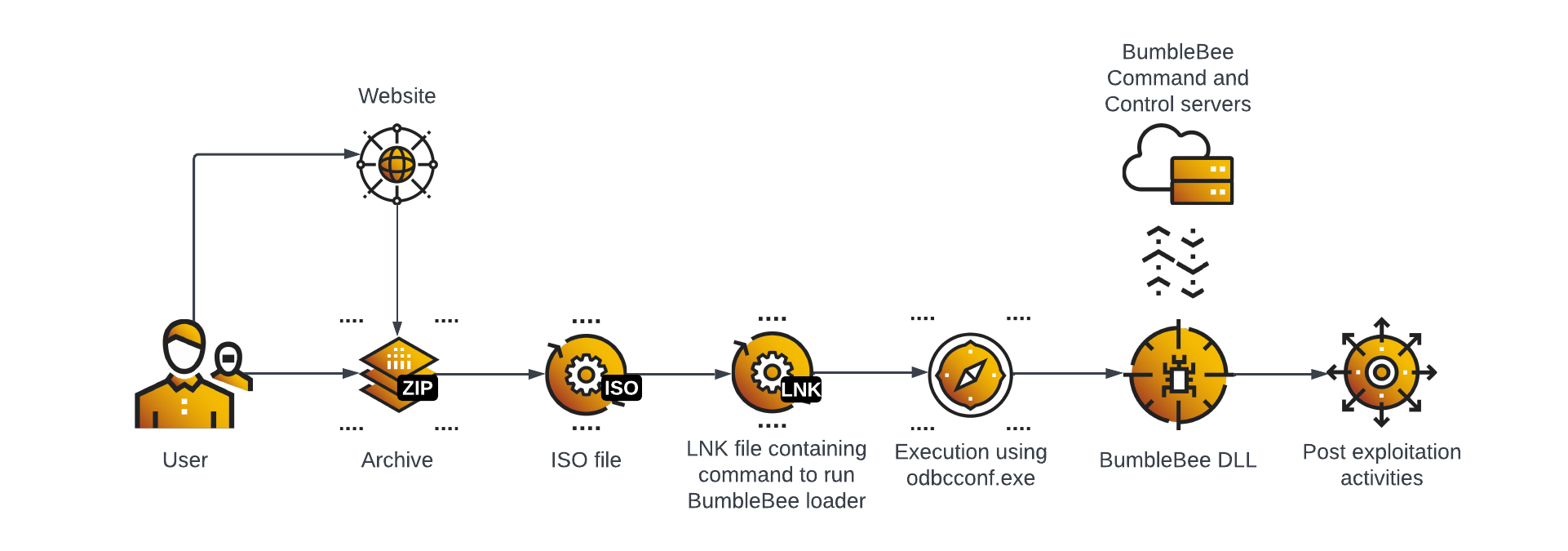
THREAT ANALYSIS REPORT: Bumblebee Loader – The High Road to

Introducing Advanced Response Actions - F-Secure Blog

Traders' dollars in danger: CVE-2023-38831 zero-day vulnerability

Deconstructing Amadey's Latest Multi-Stage Attack and Malware

Phorpiex morphs: How a longstanding botnet persists and thrives in

Unpacking RDStealer: An Exfiltration Malware Targeting RDP Workloads

Chinese Cyberespionage Group BRONZE SILHOUETTE Targets U.S.

Blind Eagle Deploys Fake UUE Files and Fsociety to Target
How 4 Types of Cyber Threats Break Your Online Security [INFOGRAPHIC]
The history of encryption: the roots of modern-day cyber-security

From cookie theft to BEC: Attackers use AiTM phishing sites as

RTF Template Injection: Phishing Attachment Techniques
Recomendado para você
-
 Start typing random text to simulate that you're hacking a computer system. Discover the programs clicking the icons on th…28 outubro 2024
Start typing random text to simulate that you're hacking a computer system. Discover the programs clicking the icons on th…28 outubro 2024 -
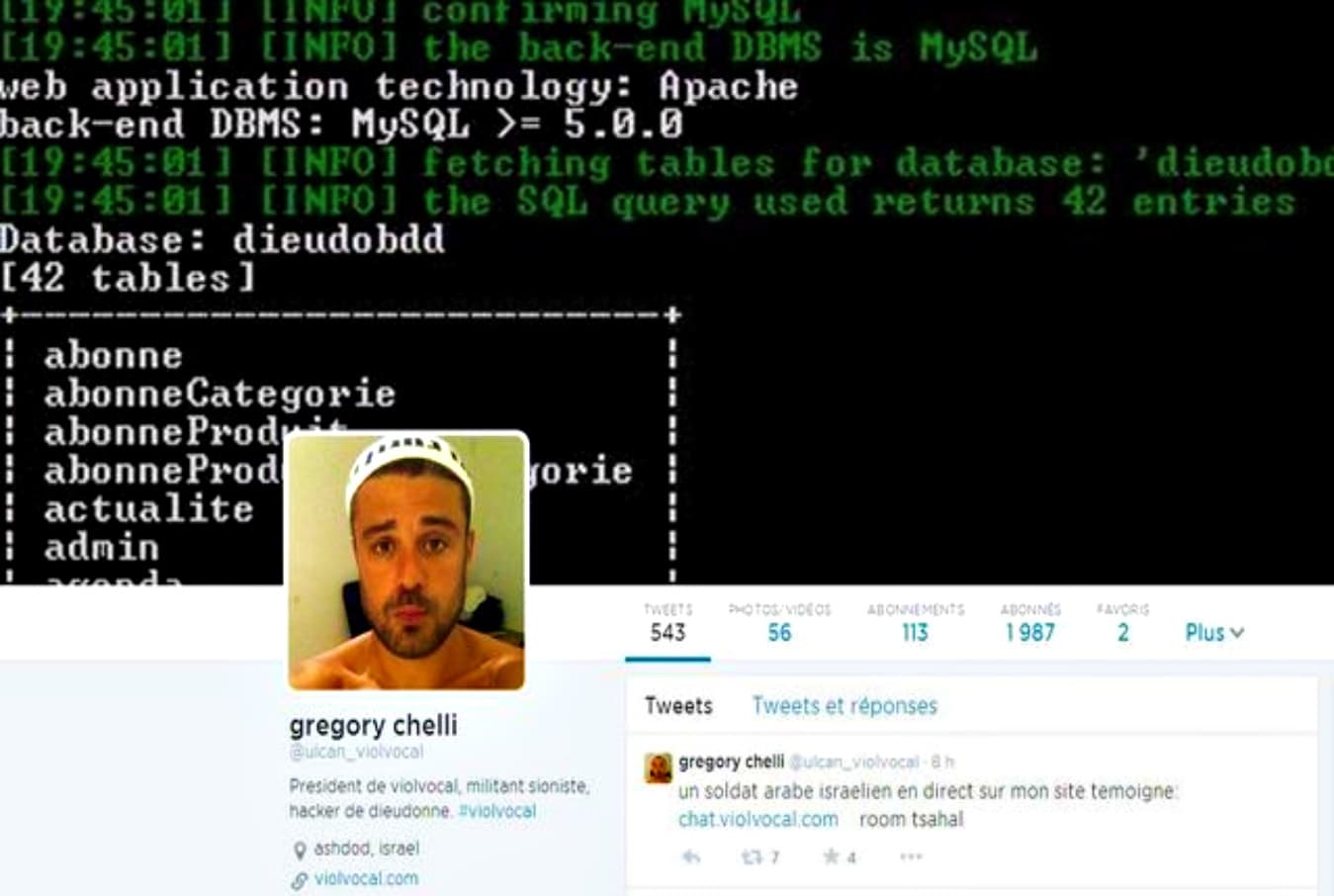 Death linked to prank - France seeks extradition of hacker from Israel28 outubro 2024
Death linked to prank - France seeks extradition of hacker from Israel28 outubro 2024 -
 What is a Black-Hat Hacker?28 outubro 2024
What is a Black-Hat Hacker?28 outubro 2024 -
 Anonymous Indonesia' Launches Cyber Attack on Government Sites28 outubro 2024
Anonymous Indonesia' Launches Cyber Attack on Government Sites28 outubro 2024 -
Hackers - latest news, breaking stories and comment - The Independent28 outubro 2024
-
 Meet 'swatting,' the dangerous prank that could get someone killed28 outubro 2024
Meet 'swatting,' the dangerous prank that could get someone killed28 outubro 2024 -
Did You Get an Email That Says You've Been Hacked?28 outubro 2024
-
 Wifi Password Hacker::Appstore for Android28 outubro 2024
Wifi Password Hacker::Appstore for Android28 outubro 2024 -
 Android Users: Pakistan-linked hackers using these three apps to target Android users in India - Times of India28 outubro 2024
Android Users: Pakistan-linked hackers using these three apps to target Android users in India - Times of India28 outubro 2024 -
 iPhone Camera Hacked: Three Zero-Days Used In $75,000 Attack Chain28 outubro 2024
iPhone Camera Hacked: Three Zero-Days Used In $75,000 Attack Chain28 outubro 2024
você pode gostar
-
 kozel.unovarpg.com - UnovaRPG (Pokemon Indigo) - On - Kozel UnovaRPG28 outubro 2024
kozel.unovarpg.com - UnovaRPG (Pokemon Indigo) - On - Kozel UnovaRPG28 outubro 2024 -
 Call Of Duty Ghost Mask Skull Patches, Diy Embroidery Decorative28 outubro 2024
Call Of Duty Ghost Mask Skull Patches, Diy Embroidery Decorative28 outubro 2024 -
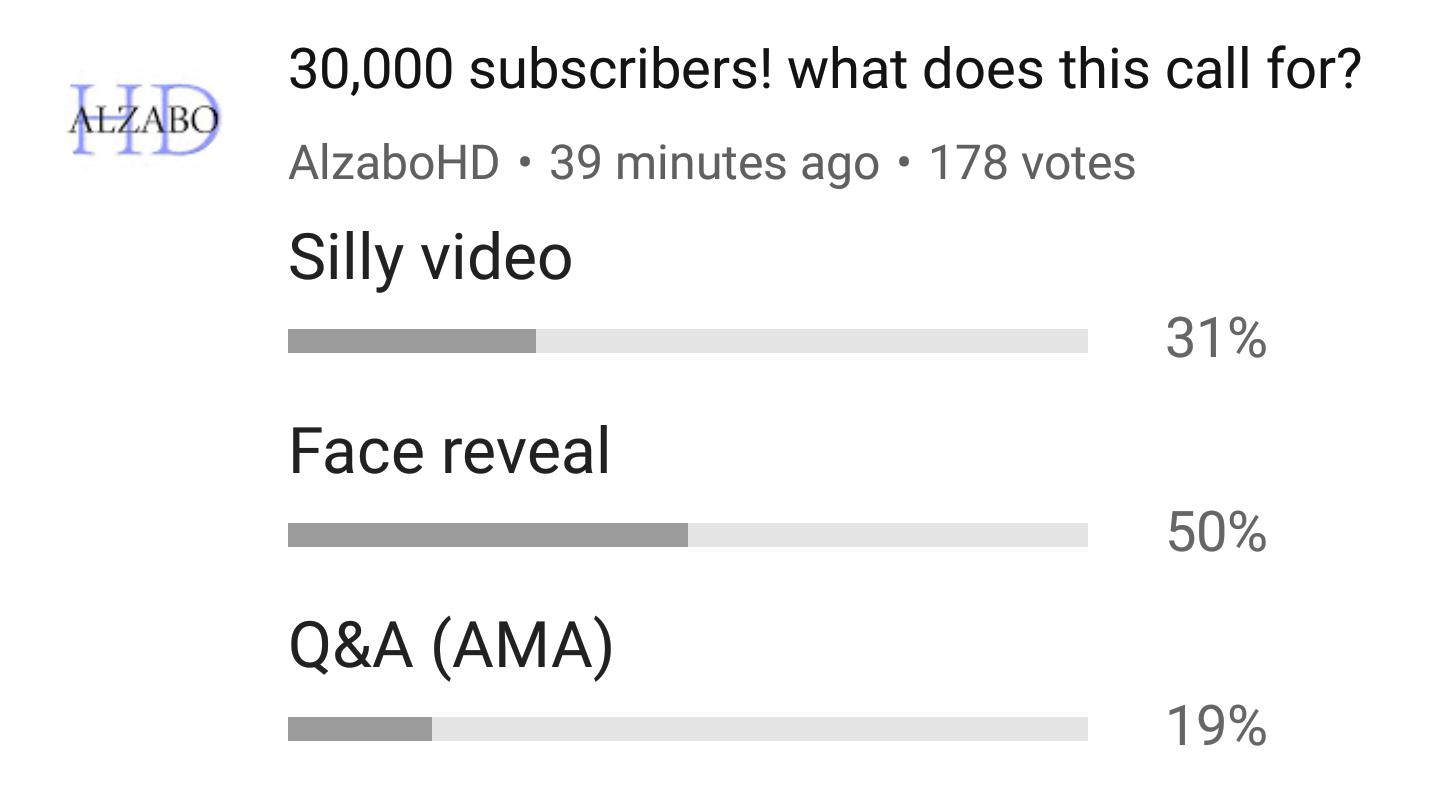 AlzaboHD on X: Silly face reveal? Check out the poll on my YT28 outubro 2024
AlzaboHD on X: Silly face reveal? Check out the poll on my YT28 outubro 2024 -
 Which Minecraft skin do you like better { The elements are on the left arm } : r/minecraftskins28 outubro 2024
Which Minecraft skin do you like better { The elements are on the left arm } : r/minecraftskins28 outubro 2024 -
 Home Roblox by Num-Kirby on DeviantArt28 outubro 2024
Home Roblox by Num-Kirby on DeviantArt28 outubro 2024 -
 CRYZEN.IO jogo online gratuito em28 outubro 2024
CRYZEN.IO jogo online gratuito em28 outubro 2024 -
 Create meme roblox t shirts suit, shirt roblox, roblox t shirt28 outubro 2024
Create meme roblox t shirts suit, shirt roblox, roblox t shirt28 outubro 2024 -
 My dog stepped on a bee” : r/dankmemes28 outubro 2024
My dog stepped on a bee” : r/dankmemes28 outubro 2024 -
 Can You Use GPS Joystick To Spoof In Monster Hunter Now?28 outubro 2024
Can You Use GPS Joystick To Spoof In Monster Hunter Now?28 outubro 2024 -
 DualSense Edge, o novo comando da Playstation 528 outubro 2024
DualSense Edge, o novo comando da Playstation 528 outubro 2024
