Malware analysis Suspicious activity
Por um escritor misterioso
Last updated 24 outubro 2024
Detections and alerts, Elastic Security Solution [8.11]

Advanced Malware Detection – Signatures vs. Behavior Analysis
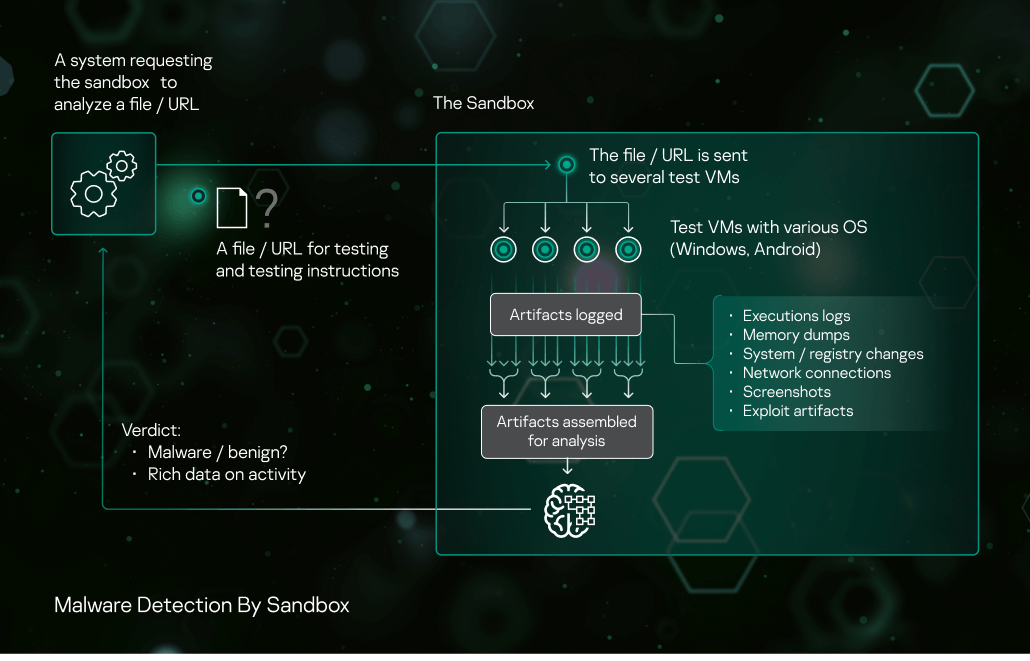
Sandbox Kaspersky

Microsoft 365 Alerting - Detect and React to Threats Instantly
Highlight, take notes, and search in the book

Mastering Malware Analysis: A malware analyst's practical guide to combating malicious software, APT, cybercrime, and IoT attacks, 2nd Edition

Behavioral blocking and containment: Transforming optics into

How Malware Analysis Works - NetWitness Community - 669511

7 Benefits Of Dynamic Malware Analysis

Malware Analysis: Static vs. Dynamic and 4 Critical Best Practices

10 Best Malware Analysis Tools - Updated 2023! (Paid & Free)

Malware Analysis: Steps & Examples - CrowdStrike
Recomendado para você
-
FRONTLINES - Roblox24 outubro 2024
-
 Hack Week 2022: Putting Our Values into Action - Roblox Blog24 outubro 2024
Hack Week 2022: Putting Our Values into Action - Roblox Blog24 outubro 2024 -
roblox-exploit · GitHub Topics · GitHub24 outubro 2024
-
 download hack robux roblox|TikTok Search24 outubro 2024
download hack robux roblox|TikTok Search24 outubro 2024 -
 Why You Should Avoid Roblox Hack V3.7 Download 70 Մամուլի խոսնակ - Անկախ հրապարակումների հարթակ24 outubro 2024
Why You Should Avoid Roblox Hack V3.7 Download 70 Մամուլի խոսնակ - Անկախ հրապարակումների հարթակ24 outubro 2024 -
 Roblox Hack Roblox pictures, Roblox, Ios games24 outubro 2024
Roblox Hack Roblox pictures, Roblox, Ios games24 outubro 2024 -
Roblox Cursors HD24 outubro 2024
-
 Players getting kicked from my game for Exploiting - Scripting Support - Developer Forum24 outubro 2024
Players getting kicked from my game for Exploiting - Scripting Support - Developer Forum24 outubro 2024 -
 Stream Roblox Fluxus APK: Download and Play Roblox with Unlimited Features from Tara Sheldon24 outubro 2024
Stream Roblox Fluxus APK: Download and Play Roblox with Unlimited Features from Tara Sheldon24 outubro 2024 -
 Roblox: The Movie (2014) - IMDb24 outubro 2024
Roblox: The Movie (2014) - IMDb24 outubro 2024
você pode gostar
-
 O Otimista24 outubro 2024
O Otimista24 outubro 2024 -
 The Elder Scrolls VI ainda está em fase de design24 outubro 2024
The Elder Scrolls VI ainda está em fase de design24 outubro 2024 -
![Mr Robot [1920x1080] : r/wallpaper](https://preview.redd.it/7e60ub4y35n41.jpg?auto=webp&s=09d7f20e5233ba2a29db374a36dd61aafcf3b11d) Mr Robot [1920x1080] : r/wallpaper24 outubro 2024
Mr Robot [1920x1080] : r/wallpaper24 outubro 2024 -
 Anodized Steel Gold Ear Gauges Price for One Piece Screw24 outubro 2024
Anodized Steel Gold Ear Gauges Price for One Piece Screw24 outubro 2024 -
 The Best Nature for Squirtle in Pokémon FireRed and LeafGreen - Master Noobs24 outubro 2024
The Best Nature for Squirtle in Pokémon FireRed and LeafGreen - Master Noobs24 outubro 2024 -
 Exame Informática À terceira é de vez? The Last of Us II tem24 outubro 2024
Exame Informática À terceira é de vez? The Last of Us II tem24 outubro 2024 -
 Link Streaming Nonton Isekai de Cheat Skill Episode 2 Sub Indo Selain di Samehadaku dan Anoboy - Ayo Yogya24 outubro 2024
Link Streaming Nonton Isekai de Cheat Skill Episode 2 Sub Indo Selain di Samehadaku dan Anoboy - Ayo Yogya24 outubro 2024 -
 Kimetsu no Yaiba': fecha y hora de estreno España temporada 324 outubro 2024
Kimetsu no Yaiba': fecha y hora de estreno España temporada 324 outubro 2024 -
Parada do Orgulho LGBT Santos24 outubro 2024
-
 Stream vivibk, Listen to Lenga la Lenga - jogos de mãos e copos24 outubro 2024
Stream vivibk, Listen to Lenga la Lenga - jogos de mãos e copos24 outubro 2024