LetsDefend on X: Top 100 Reused Passwords / X
Por um escritor misterioso
Last updated 28 outubro 2024


Cyber Security Interview Q&A - DETECTX

LetsDefend on X: Top 100 Reused Passwords / X

log4j.pdf
Email Analysis Challenge-LetsDefend Lab Walkthrough, by Joseph Karuga
GitHub - LetsDefend/SOC-Interview-Questions: SOC Interview Questions
Malware Analysis Challenge: Analyzing malicious word document-Letsdefend, by Melusi shoko
Threat Hunting with Jupyter Notebooks— Part 1: Your First Notebook 📓, by Roberto Rodriguez
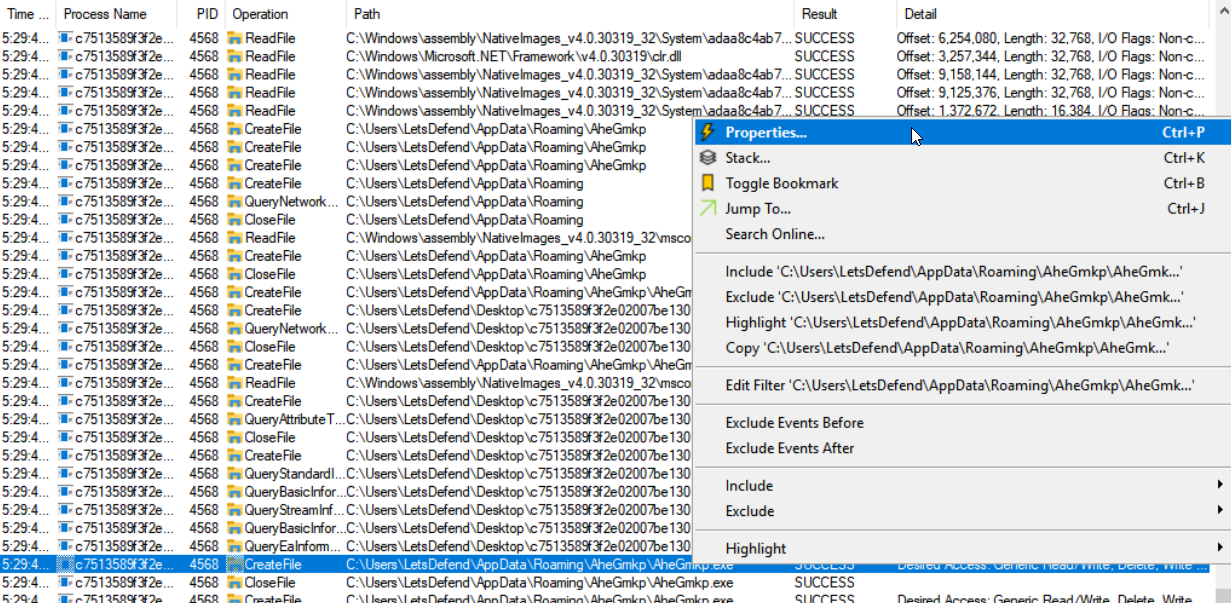
LetsDefend: Dynamic Malware Analysis Part 1, by Cybertech Maven
SOC144 EventID:91 — New scheduled task created — letsdefend.io, by Enes Adışen
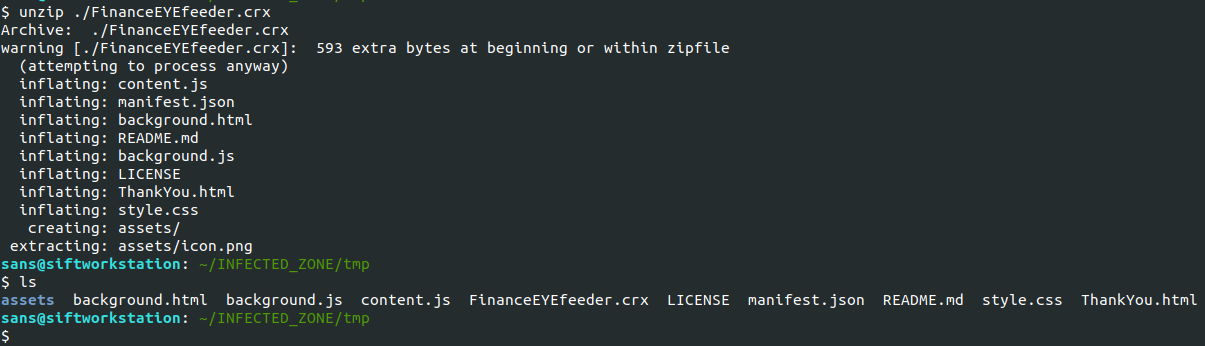
LetsDefend's Malware Analysis: Suspicious Browser Extension Walk-Through - Cyber Gladius

Harun Seker, CISSP on LinkedIn: #password #cybersecurity
Edgar Castañeda (@edgrcas) / X

LetsDefend - Blue Team Training Platform

LetsDefend's Malware Analysis: Suspicious Browser Extension Walk-Through - Cyber Gladius

Expanding digital forensics education with artifact curation and scalable, accessible exercises via the Artifact Genome Project - ScienceDirect
Recomendado para você
-
asdasd - Google My Maps28 outubro 2024
-
 OSRS Wiki button on your google search results page!!! : r/2007scape28 outubro 2024
OSRS Wiki button on your google search results page!!! : r/2007scape28 outubro 2024 -
 Unrecognized app. Please make sure you trust this app before proceeding · Issue #455 · tipsi/tipsi-stripe · GitHub28 outubro 2024
Unrecognized app. Please make sure you trust this app before proceeding · Issue #455 · tipsi/tipsi-stripe · GitHub28 outubro 2024 -
 Doodle For Google by MagicHumanDoll on DeviantArt28 outubro 2024
Doodle For Google by MagicHumanDoll on DeviantArt28 outubro 2024 -
asdas - Google My Maps28 outubro 2024
-
HubSpot Community - Free Hubspot Email Signature Template not displaying social icons properly - HubSpot Community28 outubro 2024
-
 Google Drive Backup Guide: How to backup google drive securely28 outubro 2024
Google Drive Backup Guide: How to backup google drive securely28 outubro 2024 -
 asdasdsa - Edwinius - Medium28 outubro 2024
asdasdsa - Edwinius - Medium28 outubro 2024 -
 How to Recover SEO of Hacked Sites?28 outubro 2024
How to Recover SEO of Hacked Sites?28 outubro 2024 -
asdasd Live Subscriber Count, Real-Time Subscriber Analytics28 outubro 2024
você pode gostar
-
 Reckoning Trailer, Season 528 outubro 2024
Reckoning Trailer, Season 528 outubro 2024 -
 Modern Warfare 2 could bring back Call of Duty's worst villain28 outubro 2024
Modern Warfare 2 could bring back Call of Duty's worst villain28 outubro 2024 -
 Anime Souls P2W(Seasons 2 Day 5) Most amount of Rebirths EVER DONE!28 outubro 2024
Anime Souls P2W(Seasons 2 Day 5) Most amount of Rebirths EVER DONE!28 outubro 2024 -
/i.s3.glbimg.com/v1/AUTH_08fbf48bc0524877943fe86e43087e7a/internal_photos/bs/2019/T/h/y7T8ZUTT6NwVBCCZYRvQ/apex-legends-keyart.jpg) Apex Legends: conheça os personagens do Battle Royale28 outubro 2024
Apex Legends: conheça os personagens do Battle Royale28 outubro 2024 -
 How to get the Hogwarts Legacy Cursed Tomb treasure28 outubro 2024
How to get the Hogwarts Legacy Cursed Tomb treasure28 outubro 2024 -
RTX 3070 vs RX 6800 XT Game Performance Benchmarks (Core i9-10900K vs Core i9-10900K) - GPUCheck United States / USA28 outubro 2024
-
AIRMESH HUB, Cooper Lighting Solutions28 outubro 2024
-
 Có 0 bài viết MOGO Khuyên liên quan đến do tap gym danh cho nam28 outubro 2024
Có 0 bài viết MOGO Khuyên liên quan đến do tap gym danh cho nam28 outubro 2024 -
 Hades originalmente teria Teseu como protagonista28 outubro 2024
Hades originalmente teria Teseu como protagonista28 outubro 2024 -
Pokémon Adventures (Emerald), Vol. 27 by Hidenori Kusaka, Paperback | Pangobooks28 outubro 2024


